题目
https://gitee.com/csomebro/ctftask/blob/master/2022-04_%2ACTF/examination.zip
解题
角色扮演的pwn题,可以切换学生和老师
发现了好多漏洞,估计是考漏洞的利用,当然解法可能就不止一种
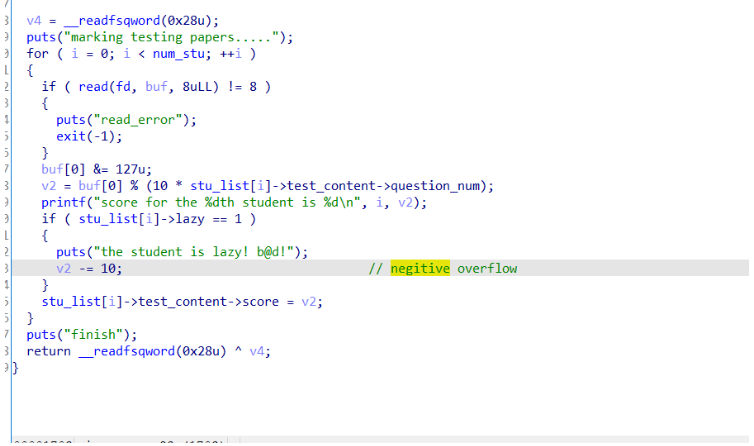
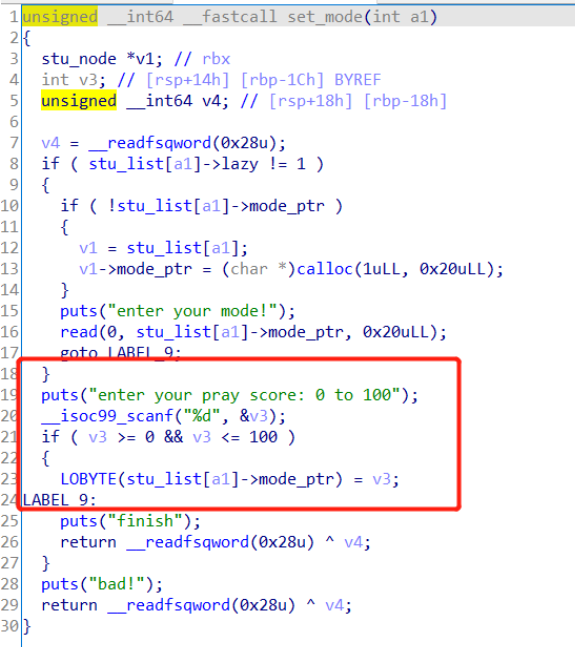
主要利用的漏洞:无符号数减法负数溢出,student role下的set mode中可以修改内存中的指针导致堆块堆叠
只用到一次free
思路,构造一个mode chunk使得这个chunk在comment chunk1的上方,以及另一个comment chunk2在其下方,然后pray一下,将指针下移16个字节,使得可以操控comment chunk的size位置,修改size为0x421绕过tcache,释放到unsorted bin,同时布置好comment chunk2的中伪造一个size位置,这个时候重新在分配一个和comment chunk1大小相同的commend chunk就会切割unsorted bin,使得main_arena的地址向后推移,写入comment chunk2,这个时候read comment chunk2就能够泄露libc基址,同样的手法,再add student,分配的student node和test node都会切割unsorted bin中的块,这个时候切割的unsorted bin就是之前堆块堆叠导致的comment chunk2,那我们就能够控制student node和test node,修改test node中的comment地址__malloc_hook,再向malloc_hook中写入ogg,再调用teacher role的pray,就能够getshell
Exp
1 | from pwn import * |
作者: Csome
