babygame
题目附件
https://gitee.com/csomebro/ctftask/blob/master/20220-03_HFCTF/babygame.tar
分析
漏洞点就是栈溢出+格式化字符串,保护全开,需要泄露canary、函数加载地址、libc加载地址、栈地址。
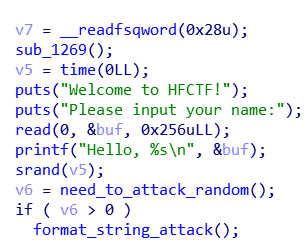
可以在read的时候将,v5的值覆盖,从而操控seed
总结
- 第一次read的时候,输入到覆盖canary的最低字节,在printf(“%s”)泄露canary地址,同时在gdb调试的时候发现同时会泄露栈地址
- attack_random之后进入格式化字符串,此时需要泄露函数加载地址,并且需要修改函数返回地址组最低位为0x39(调试的时候发现可以同时泄露libc加载地址)
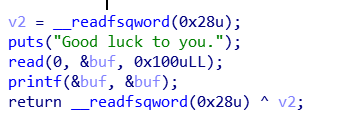
- 重新进入printf(buf)中,利用pwnlib中的fmtstr_payload修改函数返回地址到main函数开始
- 此时回到read(0, buf, 0x256),正式进入栈溢出,ret2libc。
exp
1 | from pwn import * |
小插曲:原来脚本地能跑通,远程打不通,然后我也没注意到q群有说明是更新了附件,自我分析了一点,怀疑是canary底下的栈地址本地和远程的偏移量不同,所以写了一个偏移量的爆破。
本文采用CC-BY-SA-4.0协议,转载请注明出处
作者: Csome
作者: Csome
