题目
https://gitee.com/csomebro/ctftask/blob/master/2022-05_%E6%98%A5%E7%A7%8B%E6%9D%AF/chunzhiIot.zip
解题
简单的UAF堆题,套上了一个解析Http请求的背景,首先需要逆向找到合适的构造http请求头的方法,找到堆题经典增删查改的函数,发现删除操作中没有清空指针。故可以UAF。
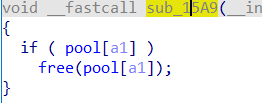
有个小细节libc 2.33之后tcache bin的fd指针加了一层加密,需要多泄露堆地址。
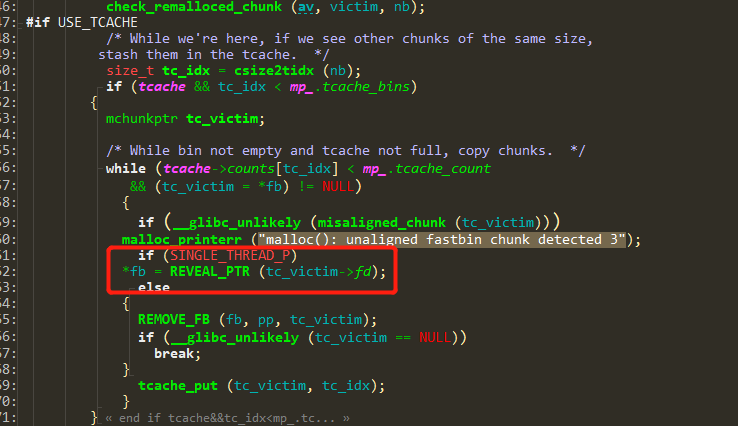
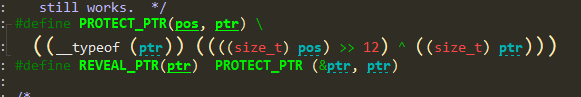
Exp
1 | from pwn import * |
第一次pwn题三血,纪念一下
本文采用CC-BY-SA-4.0协议,转载请注明出处
作者: Csome
作者: Csome
