Happytree
题目附件
https://gitee.com/csomebro/ctftask/blob/master/2022-02_SUSCTF/happytree.zip
分析
漏洞点在C++的new和delete不对堆空间进行初始化,并且delete逻辑中存在指针未清零的情况,而且存在有符号整数和无符号整数混淆,构造payload泄露main_arena和堆地址后,利用libc-2.27构造tcache的doublefree,最后new出__malloc_hook地址,写入ogg获得shell
exp
1 | from pwn import * |
rain
题目附件
https://gitee.com/csomebro/ctftask/blob/master/2022-02_SUSCTF/rain.zip
分析
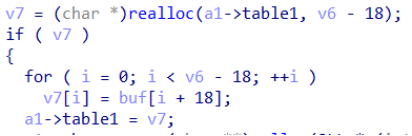
当realloc(ptr, 0)时,函数返回null,v7==0过不了if判断,故不会将指针清零,可以构造doublefree,利用doublefree和printf%s泄露在bss段上的IO_2_1_stdout地址,即可知道libc基址,最后向__free_hook写入ogg即可getshell
exp
1 | from pwn import * |
本文采用CC-BY-SA-4.0协议,转载请注明出处
作者: Csome
作者: Csome
