jmp_rsp
题目
https://gitee.com/csomebro/ctftask/blob/master/2022-05_gdCTF/jmp_rsp.zip
解题思路
直接一把梭,写入ROP,在bss上写shellcode即可
EXP
1 | from pwn import * |
midpwn
题目
https://gitee.com/csomebro/ctftask/blob/master/2022-05_gdCTF/midpwn.zip
解题思路
逆向分析发现,开了沙箱,需要利用orw进行文件内容泄露
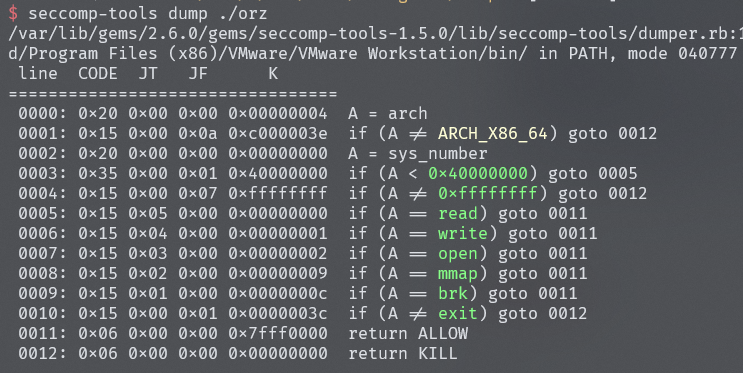
通过逆向分析发现edit函数存在off by one的漏洞
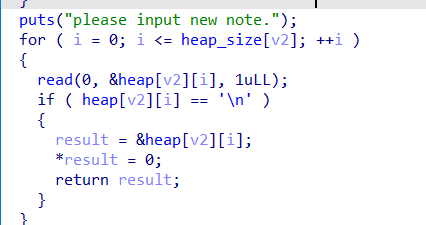
最后的思路就是,通过off by one修改下一个堆块的size位置,构造堆块堆叠,接下来主要控制tacache bin的fd指针构造任意位置分配读写。
能够实现任意位置读写之后,构造堆块进入unsortedbin,泄露main_arena的地址,从而泄露libc_base,通过偏移量算出environ的地址(libc地址中存放着environ变量,中存放着栈地址),再次构造堆块,分配到environ上面,泄露栈地址,最后,malloc执行的位置是在add函数,通过计算偏移修改add函数返回地址,写入ROP。
有关ROP的构造,实验发现mmap只需要前4个参数为addr、size、7、34即可分配出一个可执行的目标地址。
故构造ROP,分配一个0x23330000的地址作为写入shellcode的地址,最后调用read(0,0x23330000,0x50)写入orw
1 | def func(a, b, c, d): |
有关ORW的构造
1 | context(arch='amd64') |
完整EXP
1 | from pwn import * |
easyheap
题目
https://gitee.com/csomebro/ctftask/blob/master/2022-05_gdCTF/easyheap.zip
解题思路
主要漏洞在,v3局部变量可能未初始化,可以提前布置栈帧,达到任意位置写入堆地址
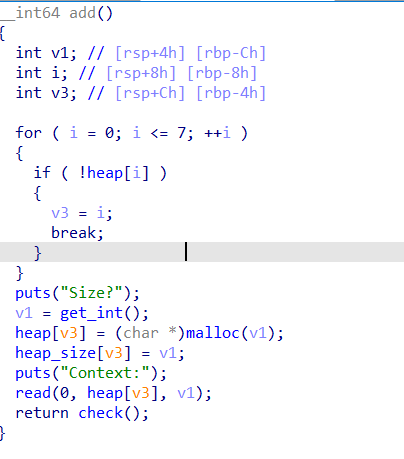
以及还有一个backdoor函数,可以堆上任意写8字节(虽然只有一次,但利用上边的漏洞可以无限次)
利用house of orange,修改IO_2_stdout,泄露libc_base,再次利用泄露environ地址,栈地址,heap基址
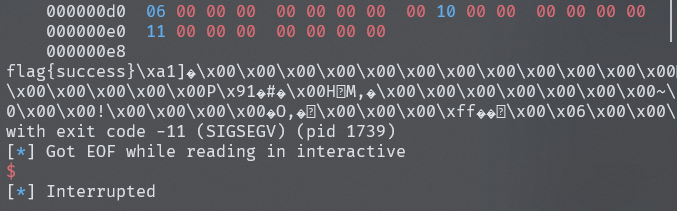
之后利用修改tcachebin上的fd指针,参考midpwn的解法,修改add函数的返回地址,写入orw ROP,获得flag
Exp
1 | from pwn import * |
其他
赛后的补题,比赛没时间了(菜),本地记得新建./flag文件
作者: Csome
