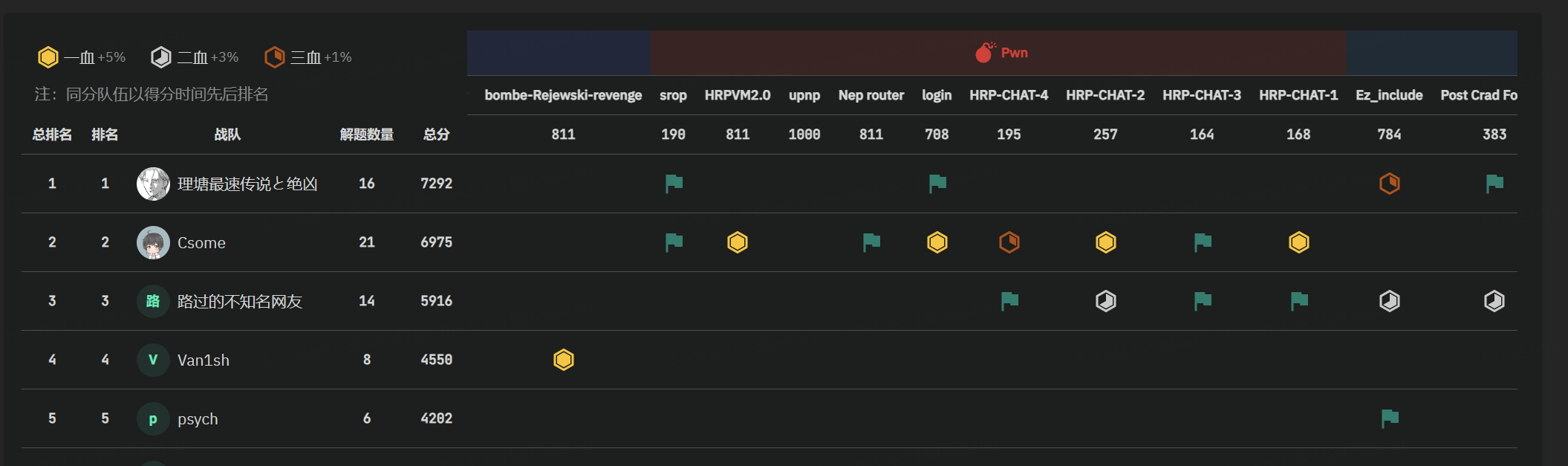
前言
纪念一下,打的很爽Pwn抢了4道一血,可惜最后3分钟第一被超了
Pwn
srop
Srop一把梭,这里要注意,跳转是PLT表的syscall函数和真实的系统调用不一样,在函数内会将rdi赋值给rax,后面的参数寄存器都要后移一位
1 | from pwn import * |
HRPVM2.0
核心思想是替换文件,这里重写了kernel文件,之后python再次调用程序就可以执行了shell了
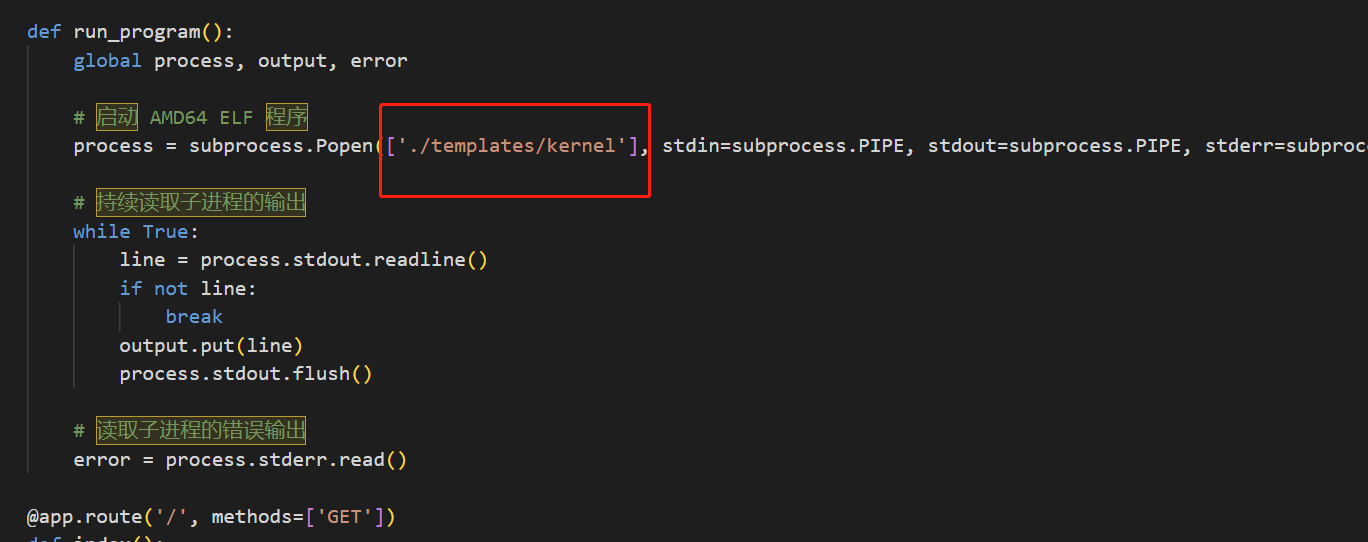
命令顺序如下,这里不能输入#,但是shell脚本使用Popen需要有shabang开头,但是shabang并不被sh执行,但输入又不能输入回车,所以这里可以采用env -S绕过
1 | mkdir app/templates |
但是mount会需要权限校验,这里需要利用溢出漏洞,off by “two”,也就是爆破1/16,踩中一个权限偏移内不为0的有效的堆地址,就可以绕过权限校验
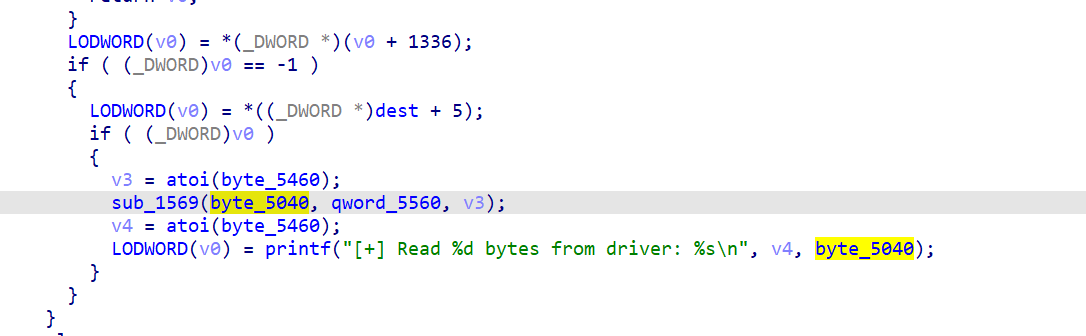
exp
1 | from pwn import * |
Nep router
https://gitee.com/baozhazhizi/IoT-vulhub/tree/master/Totolink/CVE-2022-41518
CVE-2022-41518一把梭,这里用反弹shell得到flag
1 | import contextlib |
login
首先是路径穿越,由于不会校验目录,可以直接访问文件,下载文件,最后可以下载得到login ELF文件以及libc库,之后逆向很快能看到sprintf格式化字符串漏洞,最难就是本地调试找堆指针
exp
1 | import struct |
HRP-CHAT
这一套题都是源码审计的题目,漏洞也很简单
1
SQL注入,注意这里不能用万能密码1’ or 1=1—因为在client中scanf不支持空格,所以就要先在数据库中注册一个用户名为1的用户,然后再次注册一个用户名为1'--
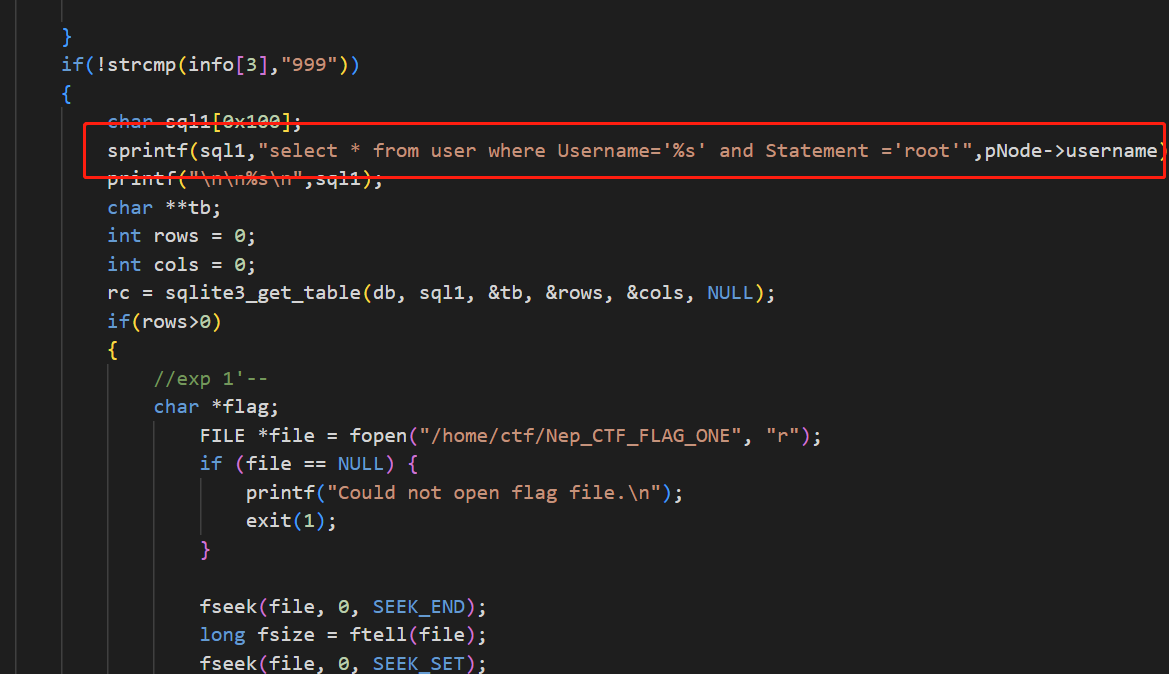
2
首先分析源码(其实也不用chat的sever,只要看client的处理逻辑即可)可以看到这里Bot模式只会返回一个字符串'远程AI协助服务正在开发中!',但是我们需要服务器返回RemoteVIPApplicationCertificationHasPassed这一串才能获得flag,那么我们就需要伪造服务器返回的message。我们可以看Chat模式下的服务器的原理,服务器就是转发消息进行广播。那么我们就可以想到
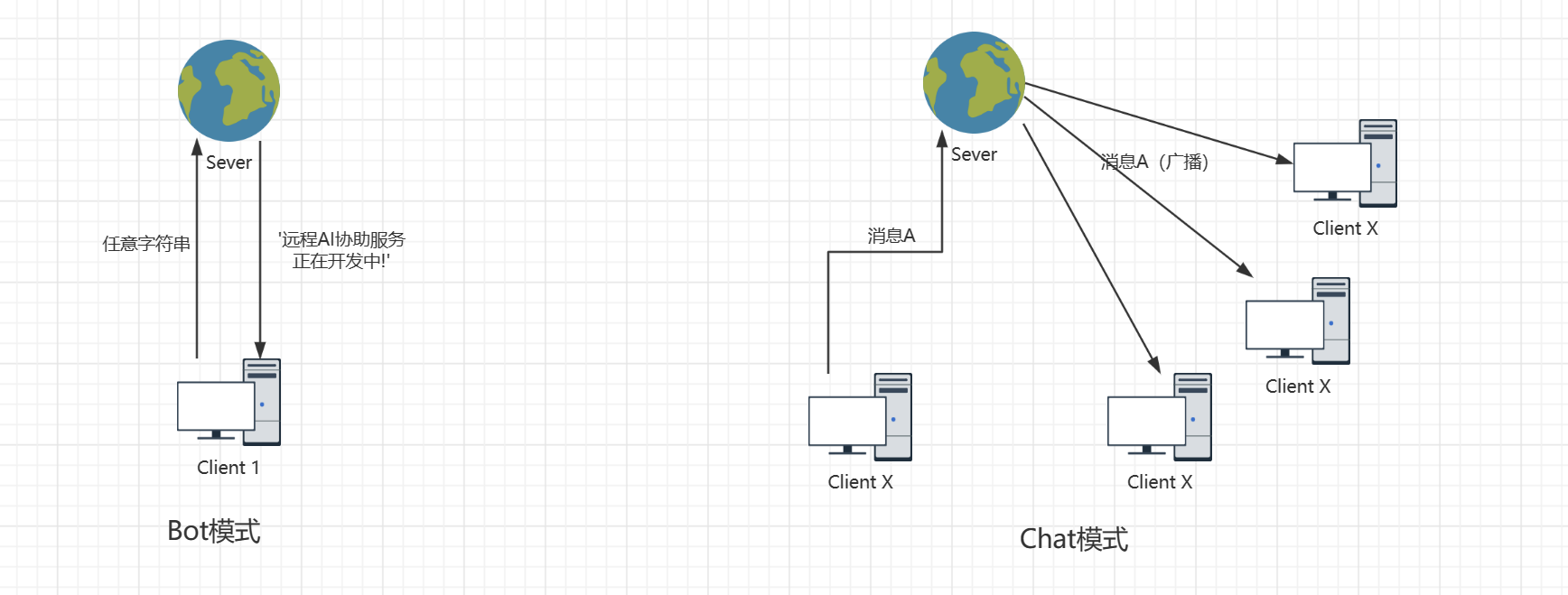
如果让一台机器在Bot模式下,另一台机器在Chat模式下
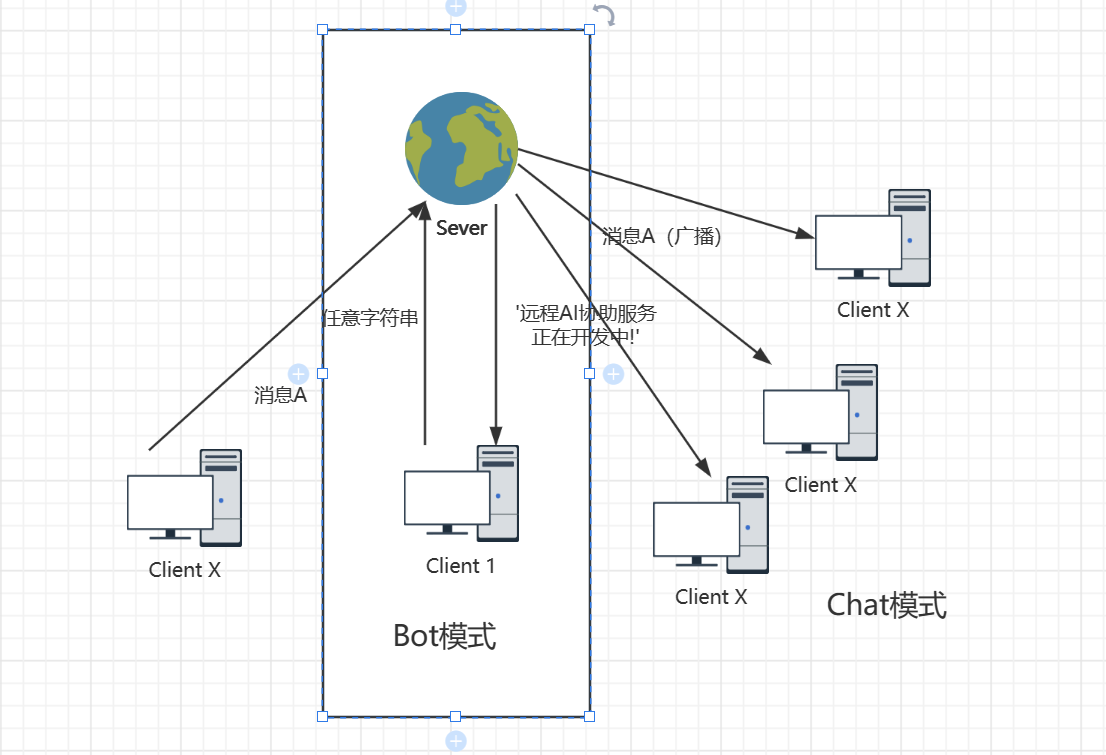
那么我们就可以利用广播的机制,伪造服务器返回message,这里也没有做任何校验,所以就能得到flag
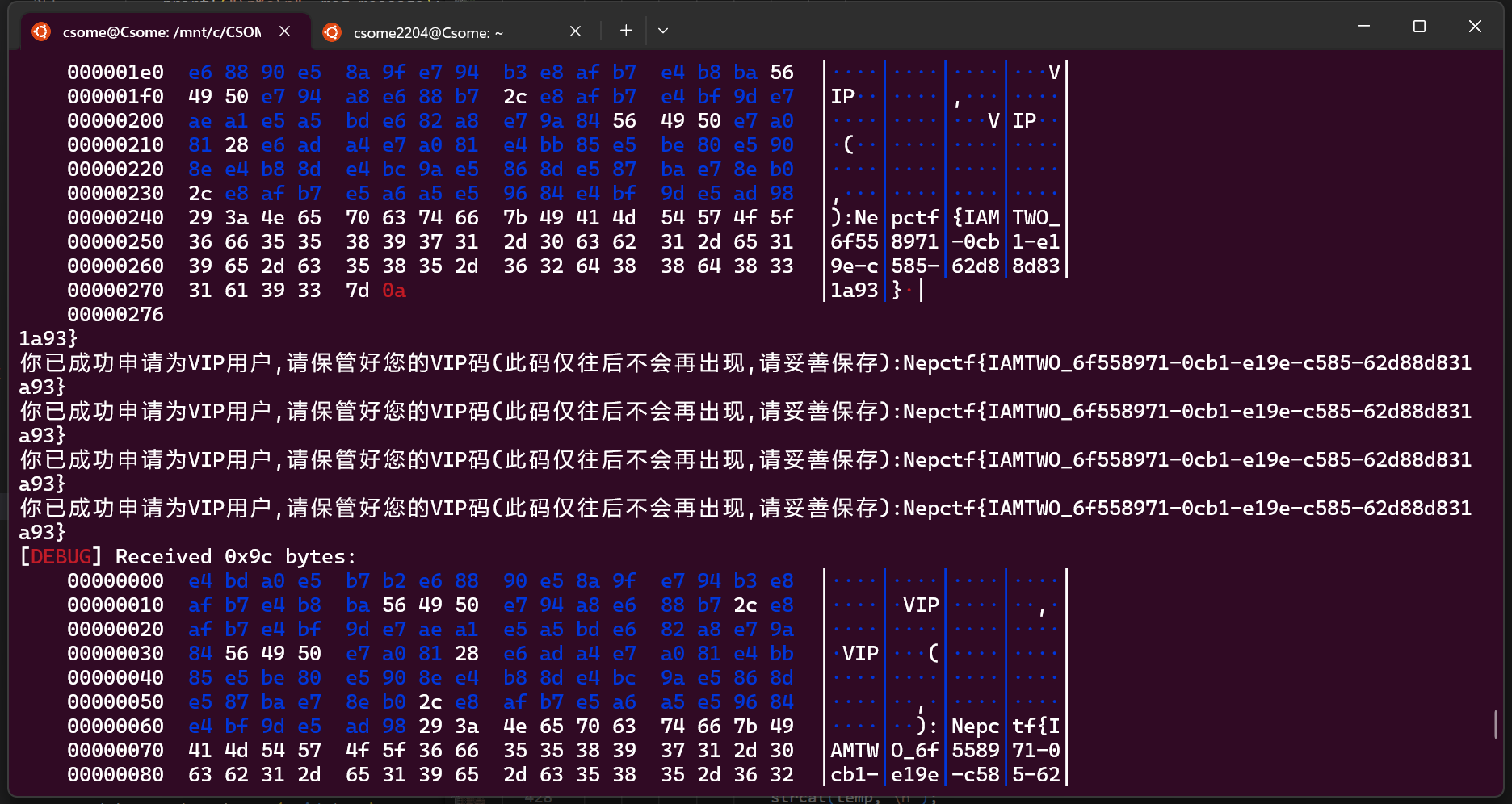
3
3号题目我看不太出来有啥漏洞,感觉就是正常的逻辑,抽卡获取角色,用message查看当前角色池子和技能,抽到H3h3QAQ就可以了,释放第二个技能log4j,就能打死ThTsOd了
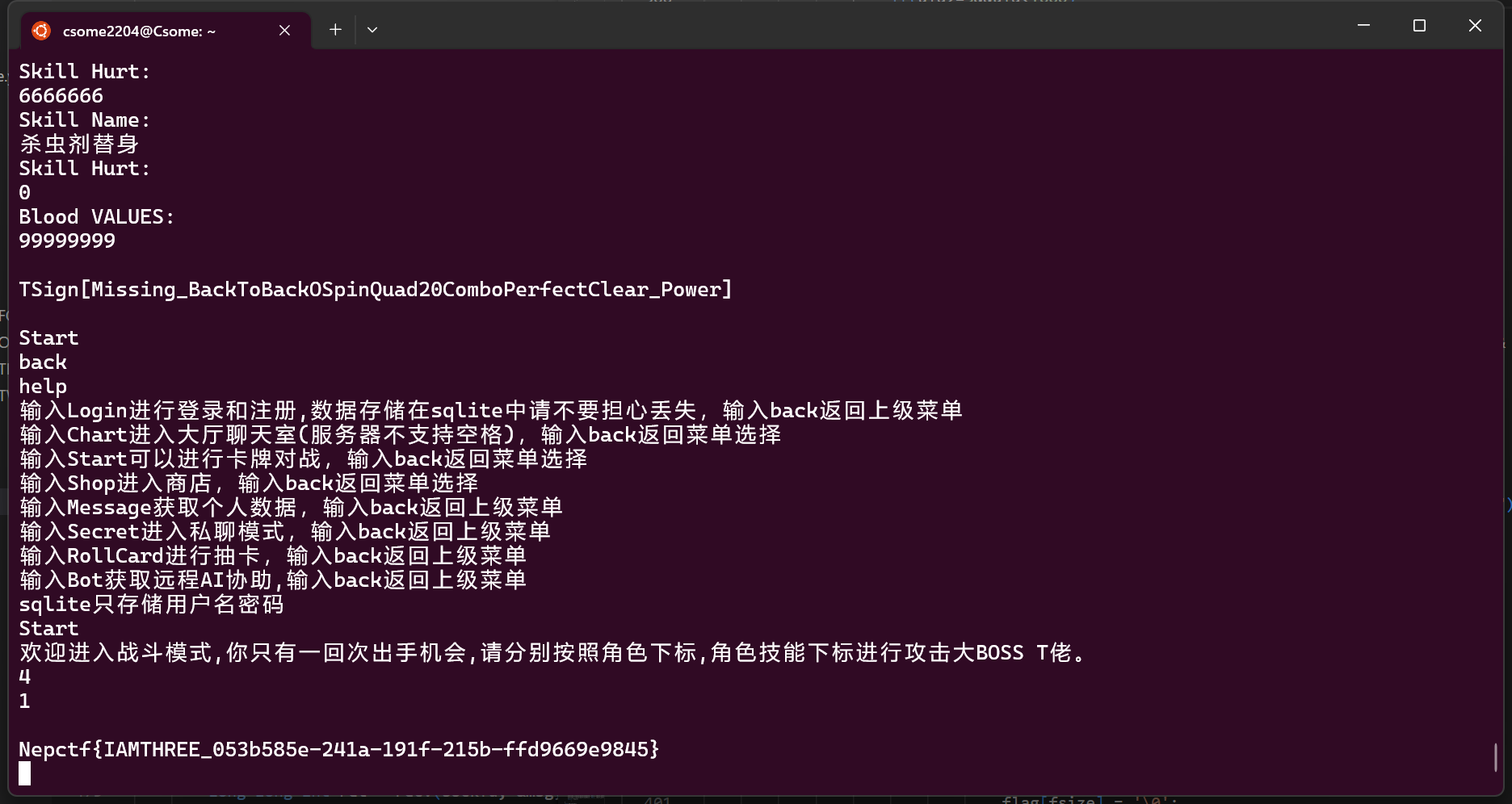
4
这个比较玄学,在我打2号flag的时候,可能是2号flag需要卡一个时机,我就写了脚本爆破,可能请求太多了,服务器就崩溃了,进入Safe box的cmd界面,输入Safe_Mode_Key就可以获得flag
Misc
codes
pwn的思路打,先泄露libc,找到偏移直接system(“env”)一把梭
1 |
|
与AI共舞的哈夫曼
确实不用自己写代码,GPT一把梭
1 | def decompress(input_file, output_file): |
ConnectedFive
万宁五子棋,注意下棋到同一个位置会死机所以要,写逻辑爆破,为了提高胜率,这里采用最朴素的策略,计算每一个空白位置自己的棋子的密度,来判断哪些位置更优
exp
1 | import random |
CheckIn
b站发不出去,等了一会儿,flag直接在题目描述了
陌生的语言

https://ay.medyotan.ga/upload/lwa_moonrunes.png
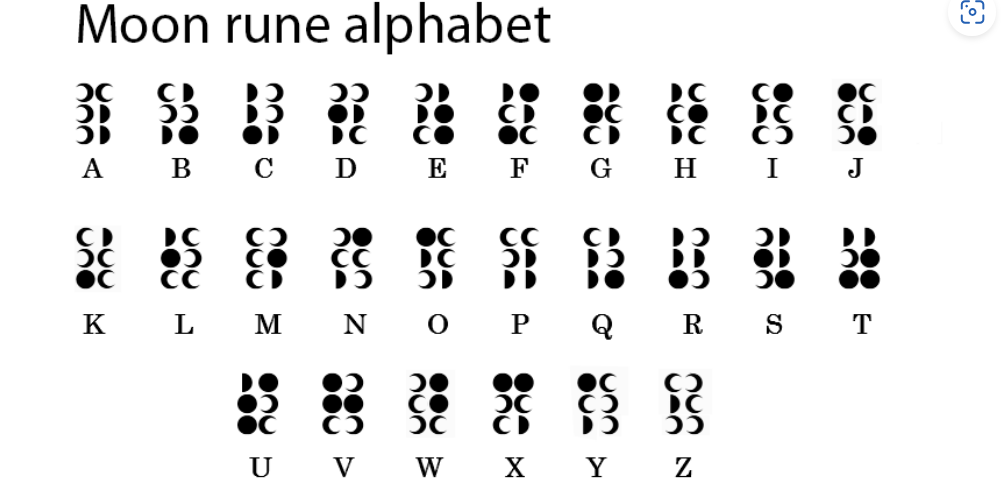
直接出
NEPNEP_A_BELIEVING_HEART_IS_YOUR_MAGIC
小叮弹钢琴
莫斯编码得到YOUSHOULDUSETHISTOXORSOMETHING,字面意思,你需要用这个xor,还有一段直接mid看
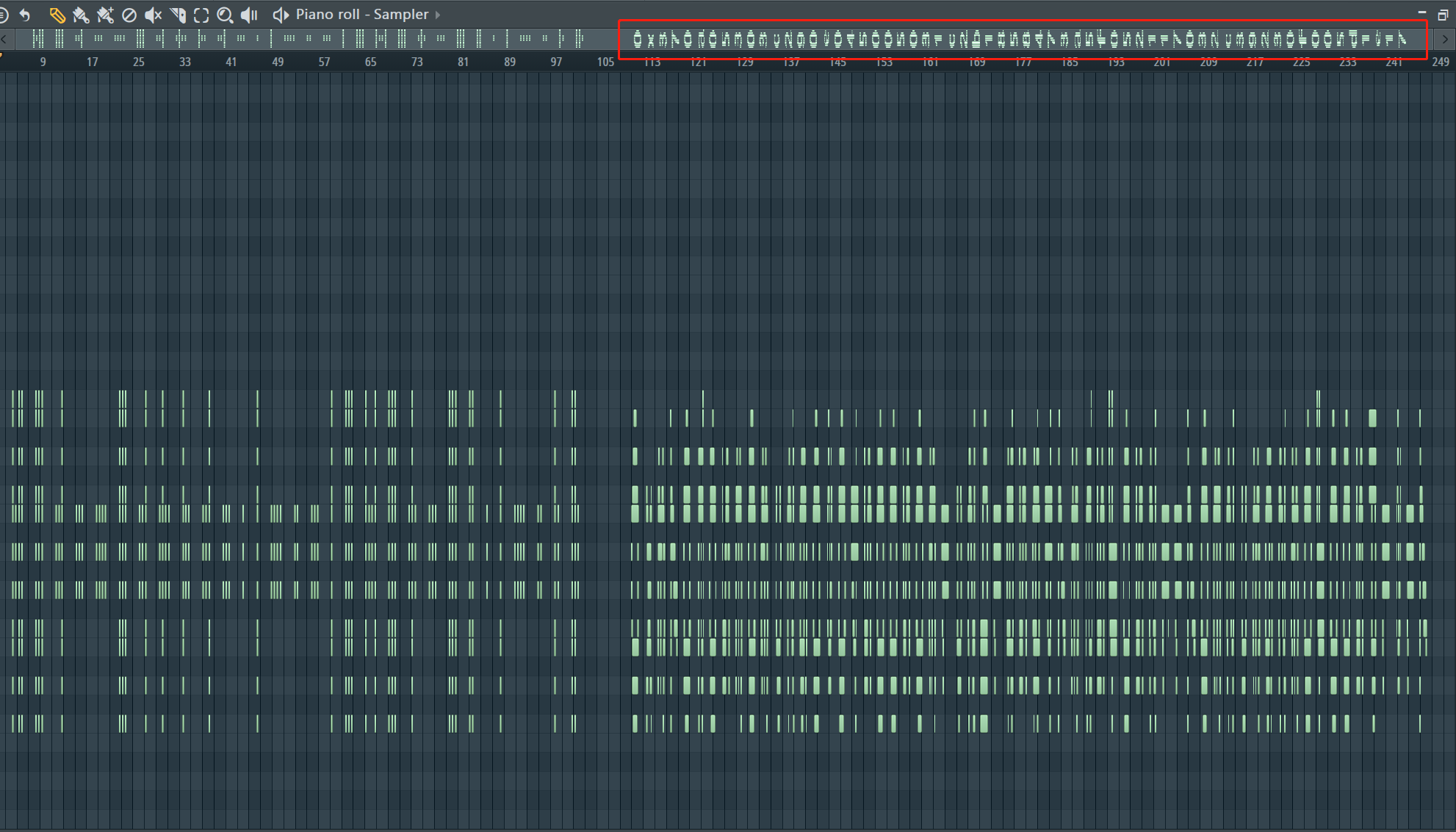
1 | x = 0x370a05303c290e045005031c2b1858473a5f052117032c39230f005d1e17 |
大小写转换异或32
你也喜欢三月七么
首先是用群名字sha256得到dd8e671df3882c5be6423cd030bd7cb69671ef27dfe7a541903edc4e23168009取前面的16个字节
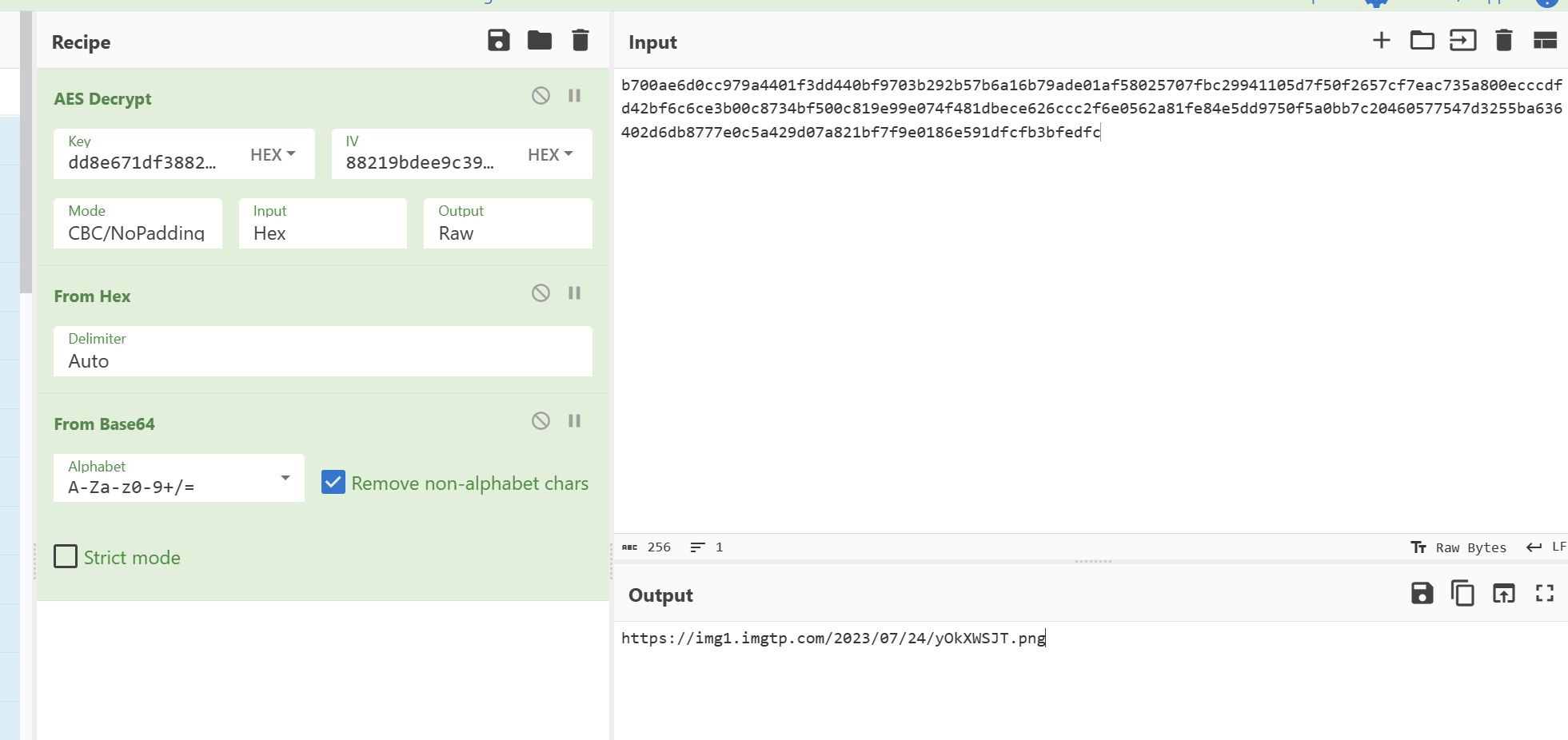
得到https://img1.imgtp.com/2023/07/24/yOkXWSJT.png

一眼星穹铁道的文字

翻译可得
HRP_aIways_likes_March_7th这里的aIways的I是大写的i
lic
磁带信息,先用audiotap转磁带文件,再用010打开
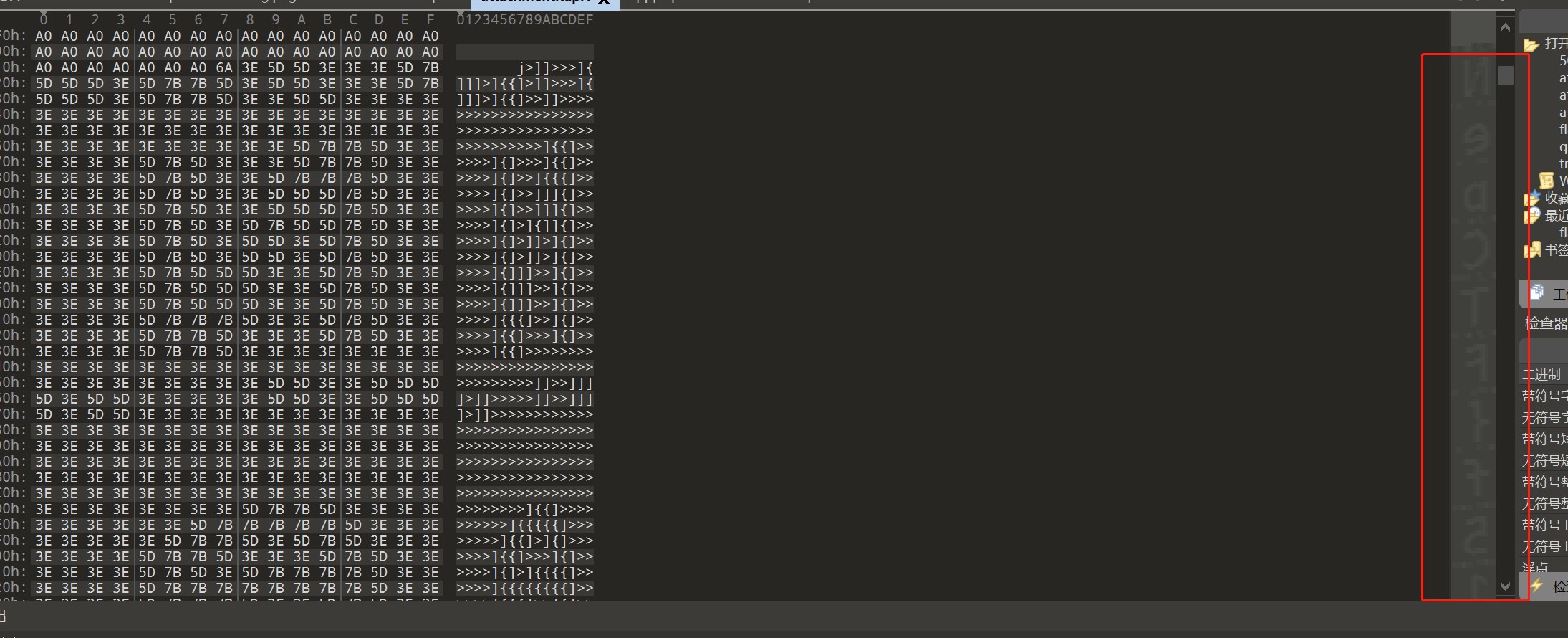
可以看到文字的NepCTF形状,利用脚本反转之后可以看到
1 | with open("attachment.tap", "rb") as f: |
Crypto
random_RSA
winner’s攻击,这里用了低指数解密算法的脚本https://github.com/pablocelayes/rsa-wiener-attack,恢复d
因为phi(n^2)近似(q^2-1)(p^2-1),先用命令交互出一组数据,之后使用下面脚本爆破
得到d之后
因为$ed-1=k(p^2-1)(q^2-1)=k(p^2q^2-p^2-q^2+1)=k(n^2-p^2-q^2+1)$
所以可以利用$(ed-1+n^2)/n$得到k
之后一把梭求p,q即可
1 | import ContinuedFractions, Arithmetic, RSAvulnerableKeyGenerator |
simple_des
爆破9位恢复L,之后逆推下面这个操作即可恢复L,R的初始,由于LR来自key其中的56位,所以只要知道key的56个bit即可
1 | for i in range(16): |
exp
1 | from operator import add |
Web
ez_java_checkin
简单的java反序列化漏洞,一把梭
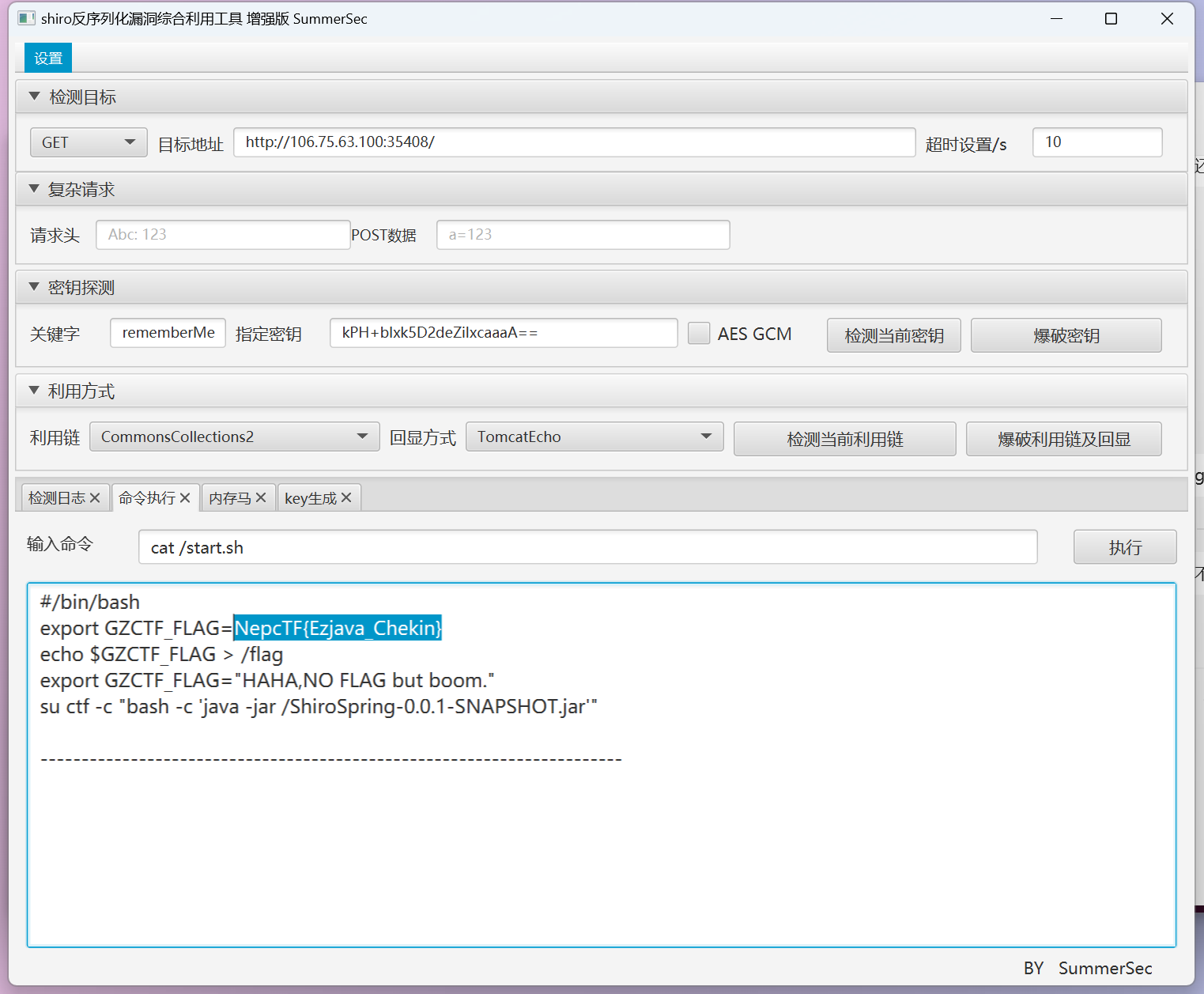
独步天下-转生成为镜花水月中的王者
渗透签到,提示环境变量提权,一把梭
1 | echo "/bin/sh"> /tmp/ports-alive |
作者: Csome
