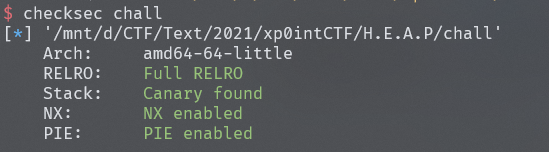
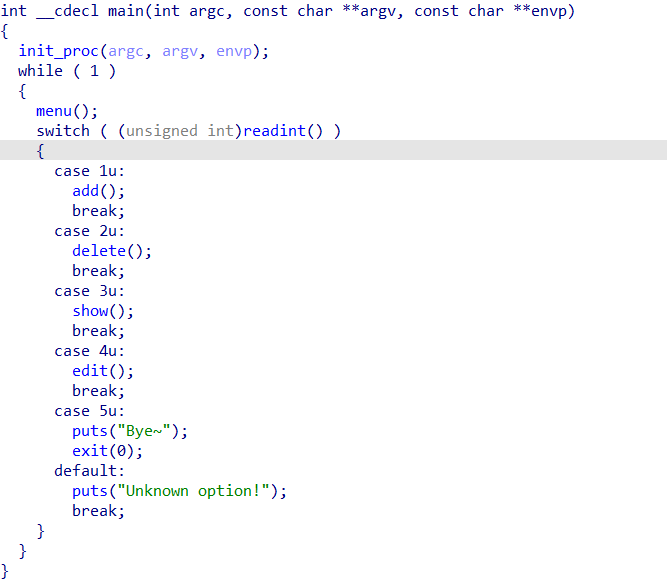
div_overflow
分析
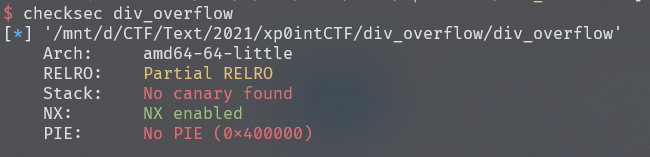
没开canary和PIE
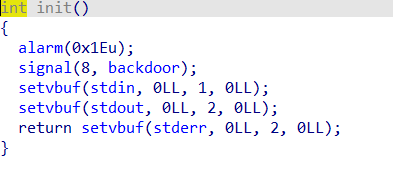
init()函数发现有一个signal绑定,
百度C 库函数 – signal() | 菜鸟教程 (runoob.com)
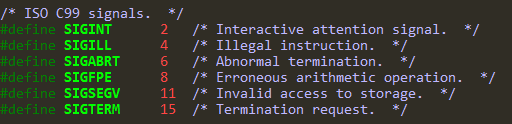
查看glibc源码可以发现,这个是将除零溢出错误信号绑定到backdoor函数上了(就是说触发这个信号,不会报错会直接跳转到对应函数运行)
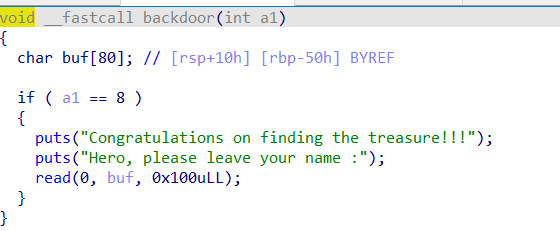
backdoor函数发现栈溢出漏洞
SIGFPE信号的触发
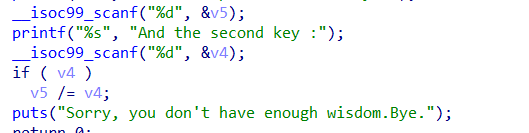
main函数过程中有一个除法运算,但需要v4不为0才能进入,那么就不能构造1/0的形式
由于计算机采用的是补码的表示方法,32位机器位可以表示的有符号整数范围为-2147483648~2,147,483,647
发现构造-2147483648/-1=2147483648,会发生除法溢出,从而进入backdoor
Exp
1 | from pwn import * |
guess
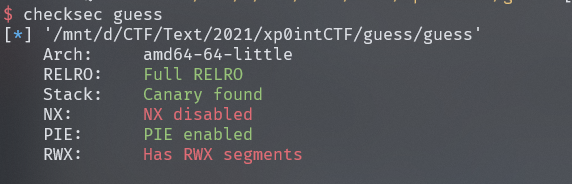
没有开NX,存在shellcode执行
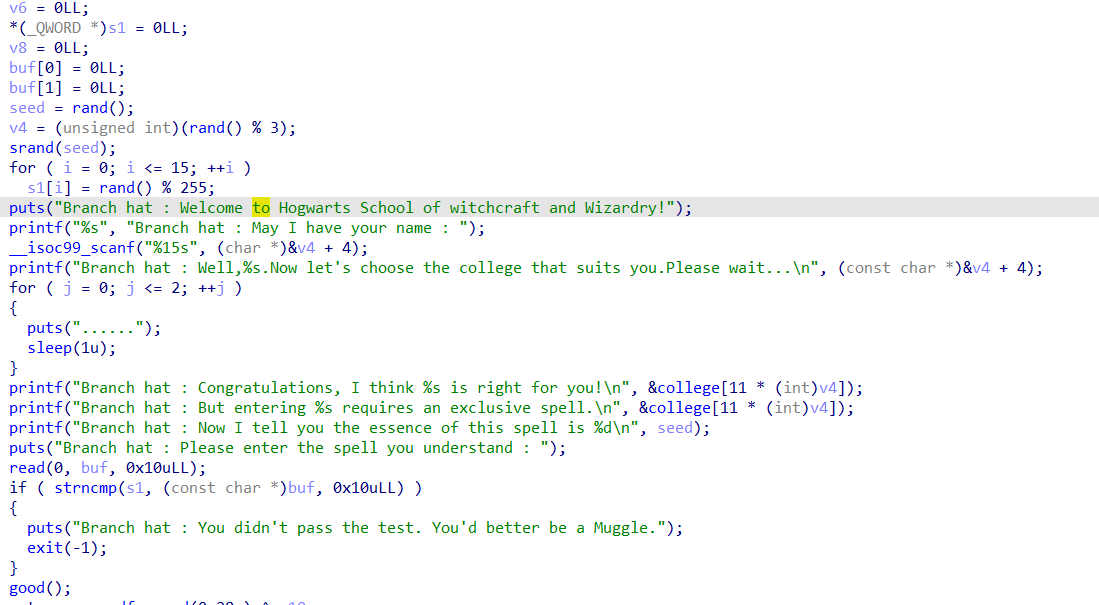
main函数调用game(),game()是主要逻辑,大概意思就是需要预测随机数,首先会使用时间播种
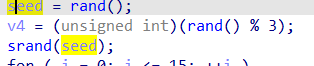
然后随机生成16个字符,并存入s中
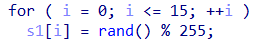
最后需要我们输入16字符和s进行校验,校验成功就可以进入good()函数
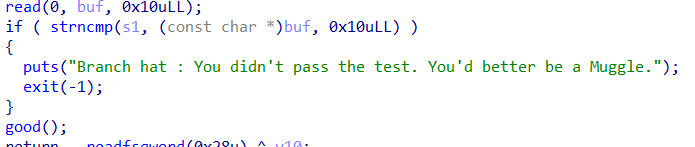
IDA分析good()函数的时候报错,只能看汇编了
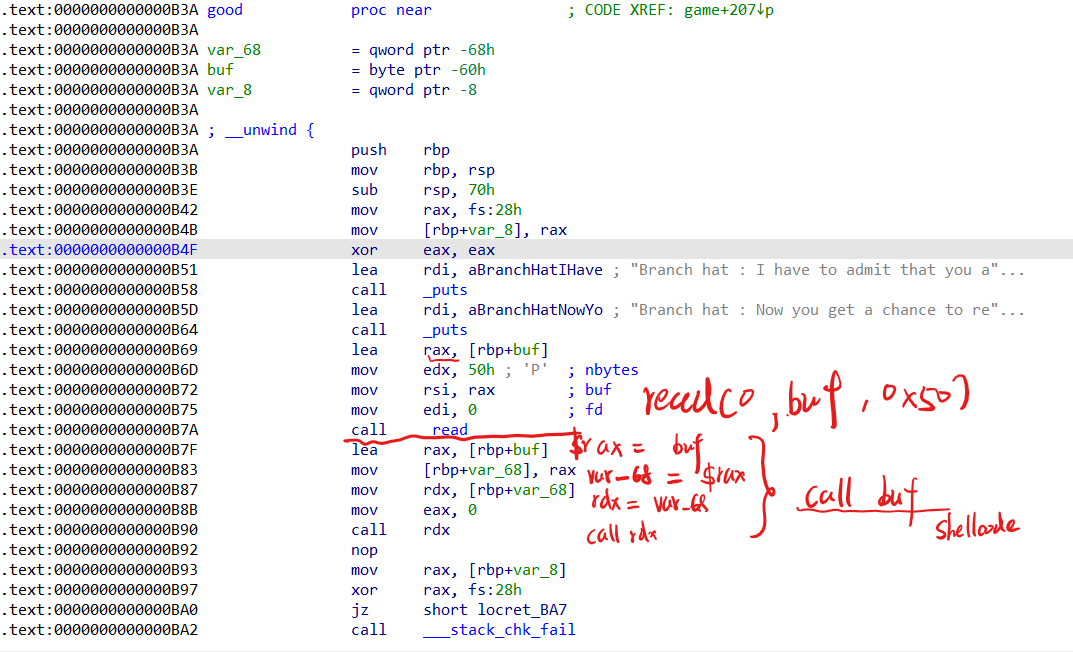
一通分析下来good函数就是shellcode后门,这样思路就很明确了,只需要预测随机数+shellcode
预测随机数
从Tover那里学来的方法,在本地写一个C程序
1 |
|
然后在服务器运行的同时运行此程序,这样就可以设置相同的seed,自然随机出来的数据就是相同的
shelldoe
Exp
1 | from pwn import * |
H.E.A.P
堆题,libc版本2.27存在tcache bin
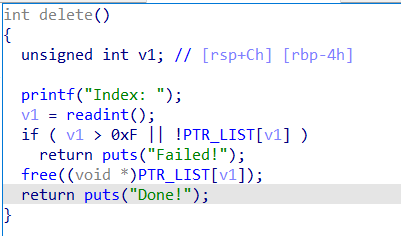
发现漏洞,free之后没有将指针清空,利用之后可以任意地址写
Exp
1 | from pwn import * |
具体利用方法见CTF pwn题堆入门 — Tcache bin_lifanxin的博客-CSDN博客
BasicMath
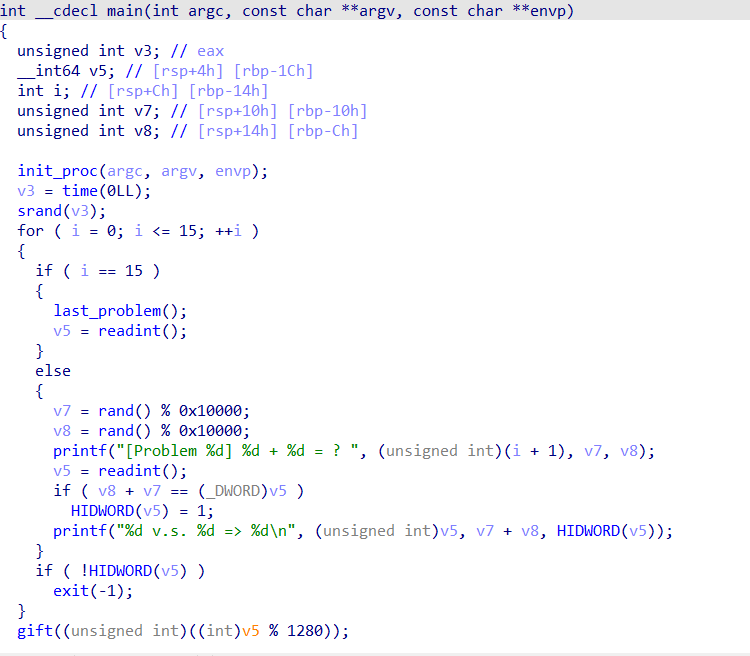
又有随机数,但这一次需要预测,直接利用python eval()计算结果就行,注意到有16个问题,当i==15是,会进入last_problem函数
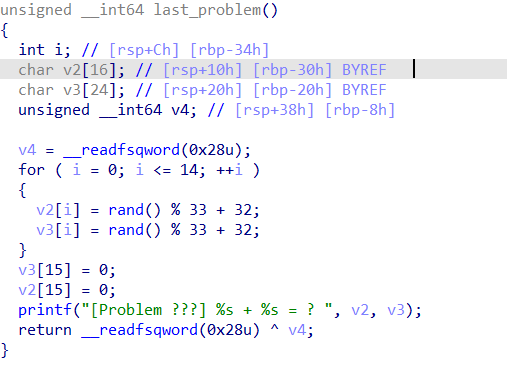
貌似没有什么问题
再仔细观察就会发现,readint返回的是64位有符号整型数
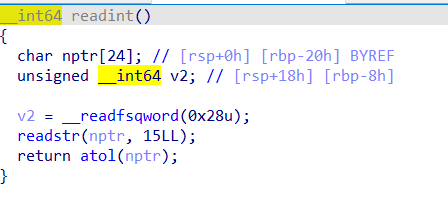
但进行校验的时候,取得是v5得高32位字节判断,所以只需要最后一次输入的数比较大就行
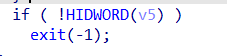
然后就是进入gift函数
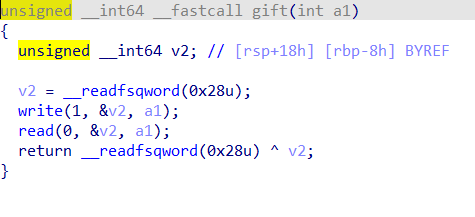
发现有leak和溢出漏洞
Exp
1 | from pwn import * |
easyheap
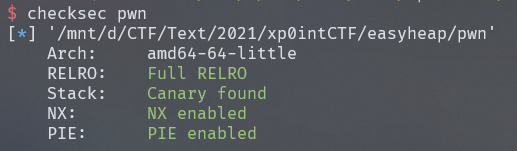
又是堆题,libc版本2.23没有tcache
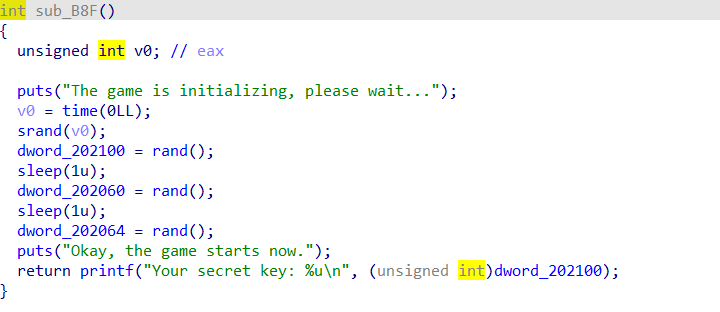
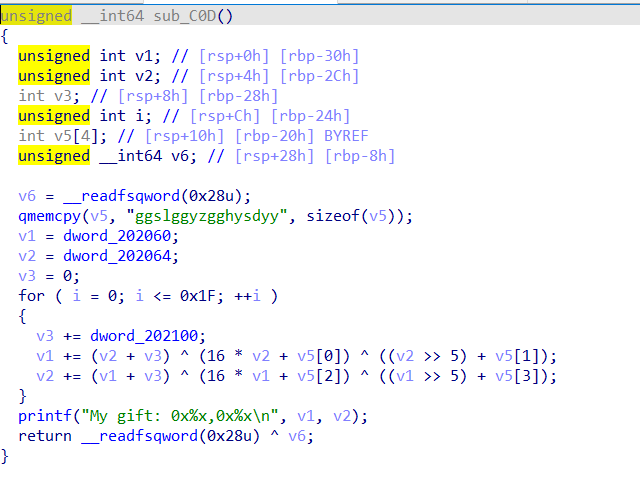
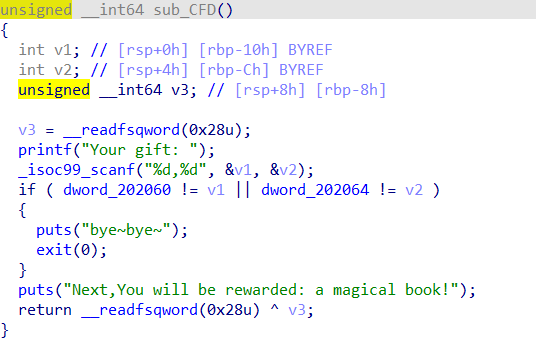
似曾相识的tea,这个题目构造貌似在那里见过?(难道是那个某省的第一届攻防大赛?)
tea解密
本地写一个c10udlnk教我的tea解密脚本
1 |
|
double free
free函数
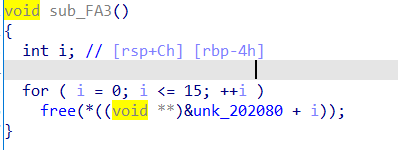
清零过程
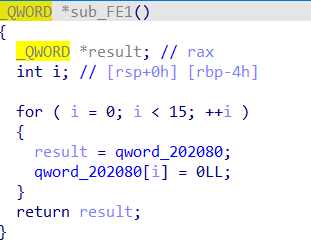
会发现第15个块,会被free但不会清零
之后就是fastbin的double free攻击
Exp
1 | from pwn import * |
fastbin double free利用方法见CTF pwn题堆入门 — Fast bin_lifanxin的博客-CSDN博客
gift
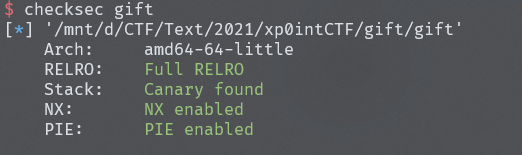
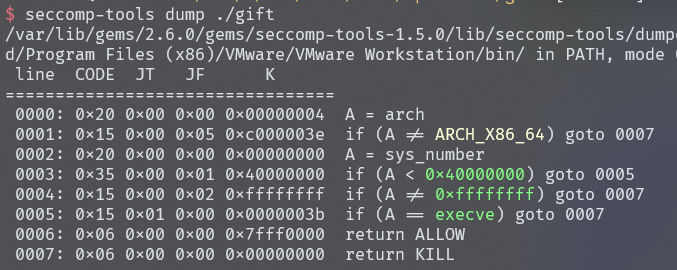
发现沙盒使用seccomp-tools,查看发现execve函数被禁用了,也就是说不能调用system、shellcode getshell这些getshell,解决方法orw(open、read、write),原理就是open打开本地文件,read读取进入内存,write打印到屏幕
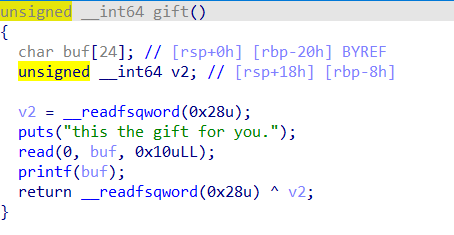
gift函数发现有一个格式化字符串漏洞,可以泄露栈地址、libc地址和函数加载地址
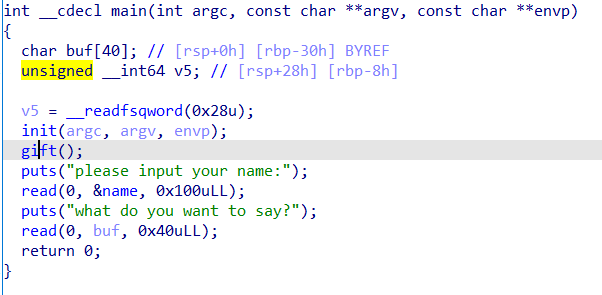
main函数发现有一个栈溢出的漏洞,但只能覆盖返回地址,不能直接构造ROP,但发现name在bss段,可以先在name函数中布置rop,然后利用两次leave;retn劫持rsp,实现栈迁移到bss,执行在name中构造的rop
ROP
rop思路首先需要实现orw,需要编写shellcode
1 | sc = asm(shellcraft.open('./flag')) |
然后需要调用libc中的mprotect函数,将bss段权限改为可读可写可执行,最后跳转到shellcode上
Exp
1 | from pwn import * |
babystack
异构pwn耶!
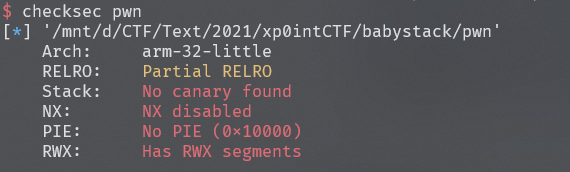
保护全关
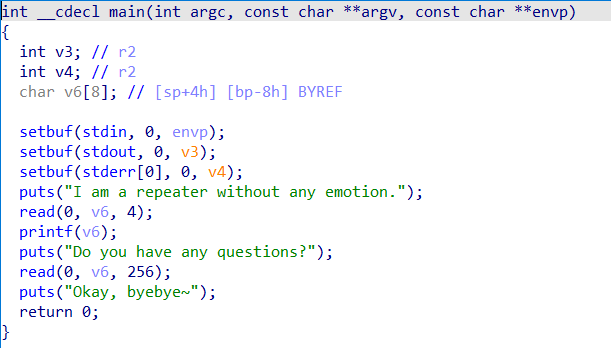
发现有一个格式化字符串漏洞,可以泄露栈地址
查阅一番资料,并看汇编发现,arm架构下PC也会存放在栈上,动态调试一番就可以算到偏移量
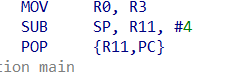
然后再v6中编写shellcode,并跳转执行即可
1 | from pwn import * |
by Csome
!!!暨南大学xp0int杯wp收集截止前禁止发送给暨南大学的同学,产生的后果由转发者承担!!!
作者: Csome
